Blog
What is Data Loss Prevention (DLP)? Trends, Types, Features, Tools and Technologies, Challenges
- May 25, 2025
- Posted by: Pawan Panwar
- Category: cybersecurity

Table of Contents
Introduction: What is Data Loss Prevention (DLP)?
Data is essential to any firm in the ongoing digital era. It is crucial to keep this priceless asset out of the wrong hands. Data Loss Prevention (DLP) is useful in this situation. Being the top cybersecurity training center in India, Craw Security is aware of how crucial DLP is to establish a strong security posture. The complexities of DLP, its importance in 2025, and how companies might use it efficiently will all be covered in this essay.
Why is Data Loss Prevention Important in 2025?
The complex threat landscape in 2025 is dynamic and getting harder to understand. The following elements highlight the increased significance of DLP:
| Escalating Cyber Threats | The frequency and sophistication of cyberattacks are increasing, and data breaches are seriously harming businesses’ finances and reputations. DLP serves as an essential line of protection against these dangers. |
| Remote Work Expansion | As remote work becomes more common, the attack surface grows, making it more difficult to keep an eye on and manage sensitive data. DLP systems go beyond the conventional network perimeter in terms of visibility and control. |
| Stringent Data Privacy Regulations | Strict data security precautions are required by regulations such as the CCPA, GDPR, and India’s own impending data protection rules. By stopping unwanted data disclosure, DLP assists enterprises in meeting these standards. |
| Insider Threats | Insider threats continue to be a major cause of data loss, whether intentional or unintentional. Unauthorized data exfiltration by workers or contractors can be identified and stopped by DLP systems. |
| Cloud Adoption | DLP solutions that may expand their protection to include data processed and stored in the cloud are required due to the increasing use of cloud services. |
Types of Data Loss and Common Threats
Implementing a successful DLP strategy requires an understanding of the many forms of data loss and the dangers that cause them:
- Exfiltration: Sensitive data being transferred or copied without authorization outside of the organization’s control. This may be unintentional (staff error) or intentional (malicious insiders, external attackers).
- Accidental Loss: Human error-related data loss includes losing unencrypted devices, deleting files, and sending emails to the incorrect recipients.
- Data Leakage: Unintentional disclosure of private information to unapproved parties, frequently brought about by improperly set up software or systems.
- Physical Loss: Loss of tangible material, such as computers, USB drives, or documents, that contain private information.
- Malware and Ransomware: Sensitive information can be destroyed, encrypted, or stolen by these malevolent programs.
Common threats include:
Some common threats include the following factors:
| Malicious Insiders | Workers or former workers who purposefully steal or divulge information. |
| External Attackers | Cybercriminals target businesses in order to steal important data for malicious or financial gain. |
| Social Engineering | Influencing others to divulge private information or engage in behaviors that jeopardize data security. |
| Phishing | Misleading emails or messages are intended to fool recipients into installing malware or disclosing private information. |
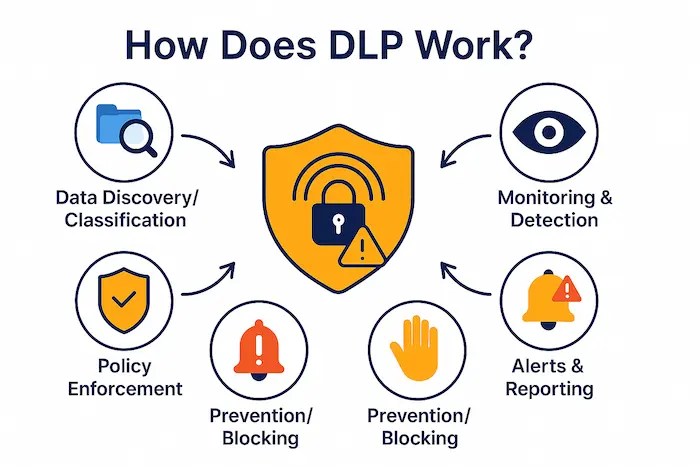
How Does DLP Work? Core Principles Explained
Sensitive data in use, motion, and rest is identified, tracked, and protected by DLP systems. The following are the fundamental ideas that guide their operations:
- Data Identification and Classification: Sensitive data must first be recognized and categorized by DLP systems using predetermined guidelines. This includes methods such as user-defined tags, contextual analysis (which assesses the location, user, and application accessing the data), and content analysis (which looks at the actual content of files and conversations). A DLP system, for instance, can be set up to identify patterns such as social security numbers, credit card information, or codenames for private projects.
- Policy Enforcement: DLP systems enforce policies that specify the usage, transport, and storage of sensitive data once it has been categorized. These regulations might be specific, outlining various guidelines according to applications, user roles, and data sensitivity levels. A policy might, for example, forbid financial data from being copied to individual USB sticks but permit its transfer to a secure shared network drive.
- Monitoring and Logging: Data-related activities are continuously monitored by DLP systems across a range of endpoints, networks, and cloud environments. By recording these activities, they provide an audit trail that can be used for compliance and investigation purposes.
- Alerting and Reporting: The DLP system creates alerts to notify security administrators instantly when a policy violation is found. In-depth reports offer information on possible hazards and trends in data security.
- Remediation: To stop data loss, DLP solutions can automatically stop unwanted file transfers, quarantine shady emails, encrypt private information, or even end user sessions.
Key Features of Effective DLP Solutions
A successful DLP system should have a number of essential components:
- Comprehensive Data Coverage: The capacity to identify and safeguard private information across networks (email, web traffic), endpoints (laptops, desktops), and cloud environments (SaaS apps, cloud storage).
- Accurate Data Identification: Using sophisticated methods to precisely identify sensitive material, such as dictionary-based analysis, content fingerprinting, and keyword matching.
- Granular Policy Management: Enabling administrators to draft comprehensive and adaptable policies according to a range of standards.
- Real-time Monitoring and Enforcement: The capacity to keep an eye on data activity and implement policies instantly to stop data loss before it starts.
- Centralized Management and Reporting: An easy-to-use interface for creating thorough reports, managing policies, and viewing alerts.
- User Behavior Monitoring: Monitoring user activity and spotting potentially dangerous patterns of conduct that could result in data loss.
- Incident Response Capabilities: Workflows and tools for efficiently responding to and fixing data loss situations.
- Integration with Other Security Tools: Smooth interaction with identity and access management systems, CASB, SIEM, and other security solutions.
Top Use Cases for DLP in Modern Businesses
Numerous data security issues in a variety of industries are addressed by DLP solutions:
| Protecting Intellectual Property (IP) | Avoiding the unapproved release of patents, corporate secrets, and other confidential data. A DLP system, for instance, has the ability to prevent unauthorized individuals from copying design papers. |
| Ensuring Regulatory Compliance | Assisting businesses in adhering to data privacy laws by stopping the disclosure of protected data, including personally identifiable information (PII). |
| Governing Sensitive Financial Data | Preventing bank account information, credit card numbers, and other financial data from being transmitted or stored without authorization. |
| Securing Healthcare Records | Preserving patient health information (PHI) while adhering to laws such as HIPAA. |
| Controlling Cloud Data | Ensuring that data exchanged and stored in cloud apps and services is secure and compliant. |
| Monitoring and Controlling Communication Channels | Preventing private information from leaking via social media, instant chat, and email. |
| Managing Removable Media | Limiting access to USB drives and other detachable storage devices in order to stop illegal data transfer. |
| Preventing Insider Threats | Identifying and stopping employees’ questionable data-related actions. |
DLP Tools and Technologies: What’s Available?
To satisfy various organizational needs, the DLP industry provides a range of tools and technologies:
- Endpoint DLP: Individual devices (desktops and laptops) have software installed to track and manage data activity.
- Network DLP: Devices or software that keep an eye on network traffic (web, email, file transfers) in order to identify and stop sensitive material from being transmitted.
- Cloud DLP: Solutions for safeguarding data utilized and stored in cloud services and apps. This can be provided as a third-party service or integrated into the cloud platform itself.
- Integrated DLP: Email security solutions, secure web gateways, firewalls, and other security products all incorporate DLP functionality.
- Data Discovery and Classification Tools: Standalone solutions that assist businesses in locating and categorizing sensitive information throughout their surroundings, an essential first step in putting DLP into practice.
Best Practices for Implementing DLP
An effective DLP program must be carefully planned and carried out. These are a few recommended practices:
| Define Clear Goals and Objectives | Determine the precise data protection issues you wish to resolve and the desired business results. |
| Understand Your Data | To determine the location and degree of sensitivity of your sensitive data, do a comprehensive data discovery and categorization exercise. |
| Develop Comprehensive Policies | Develop precise and well-defined DLP policies that satisfy both legal and business objectives. |
| Start Small and Iterate | Start with a pilot deployment that targets a particular region or kind of data, then progressively broaden the reach in response to the outcomes. |
| Educate Your Employees | Employees should receive in-depth instruction on data security procedures and the significance of DLP. |
| Regularly Review and Update Policies | Reviewing and updating your DLP policies on a regular basis is essential since business requirements and the threat landscape change. |
| Test and Fine-Tune Your Configuration | To make sure your DLP rules and configurations are efficient and reduce false positives, test them frequently. |
| Involve Stakeholders | Work together with various departments (legal, compliance, and IT) to guarantee support and handle their particular issues. |
| Monitor and Respond to Alerts | Clearly define procedures for keeping an eye on DLP alerts and handling possible data loss situations. |
Challenges and Limitations of DLP Systems
Although DLP is an effective technology, companies should be mindful of its challenges and limitations:
- Complexity of Implementation: DLP solution deployment and configuration can be difficult and time-consuming, requiring specific knowledge.
- Potential for False Positives: Excessively stringent DLP regulations may result in false positives, which would interfere with legal business operations.
- Performance Impact: System performance may be impacted by certain DLP solutions, particularly when scanning large amounts of data.
- Evasion Techniques: Advanced attackers may try to get around DLP protections by employing a variety of evasion strategies.
- User Resistance: Workers may reject and try to go around the controls if they feel that DLP is obtrusive.
- Cost: A complete DLP solution’s implementation and upkeep might be expensive.
The Future of Data Loss Prevention: Trends and Predictions
In order to handle new risks and technical developments, the field of data loss prevention is always changing. Important patterns and forecasts for the future consist of:
| Increased Integration with AI and Machine Learning | AI-driven DLP systems will advance in their ability to recognize unusual activity and more precisely identify insider threats. |
| Enhanced Cloud DLP Capabilities | DLP systems will provide more reliable and smooth data protection for multi-cloud situations as cloud use keeps increasing. |
| Focus on User and Entity Behavior Analytics (UEBA) | DLP will employ UEBA more and more to spot suspicious user activity patterns that can point to possible data breaches. |
| Data-Centric Security Approaches | A more comprehensive data-centric security approach that emphasizes safeguarding data at every stage of its lifecycle will increasingly incorporate DLP. |
| Convergence with Other Security Disciplines | A more comprehensive approach to data protection will be possible with closer integration between DLP, CASB, and other security solutions. |
| Emphasis on Data Governance and Compliance | DLP will be even more important in assisting businesses in complying with ever-tougher data privacy laws. |
FAQs
About Data Loss Prevention (DLP)
1: What is Data Loss Prevention (DLP)?
The term “data loss prevention” (DLP) describes a collection of methods, tools, and procedures intended to detect, track, and shield private information from unwanted access, use, or transmission. Preventing data loss and guaranteeing adherence to data privacy laws are the two main objectives of DLP.
2: Why is DLP important for businesses?
In order to handle the dangers of working remotely, comply with strict data privacy rules, limit insider threats, secure data in the cloud, and protect precious data from growing cyber threats, DLP is essential for businesses in 2025. Significant financial losses, harm to one’s reputation, and legal repercussions can result from data breaches.
3: How does a DLP solution work?
Sensitive data is first identified and categorized using pre-established policies in a DLP solution. It then enforces these standards to stop illegal activities like copying, sharing, or sending sensitive data while monitoring data in use, motion, and rest. The system has the ability to limit activities, issue notifications, and take other corrective measures when it detects a policy violation.
4: What types of data does DLP protect?
Personal identifiable information (PII), financial information (credit card numbers, bank account details), intellectual property (trade secrets, patents), healthcare records (PHI), private business communications, and any other information the organization deems important can all be protected by DLP.
5: What are the main causes of data loss in organizations?
Malicious insider threats, foreign cyberattacks, human error-related loss, data leakage through improperly configured systems, and the destruction of tangible media holding private data are the primary sources of data loss.
6: What are the key features to look for in a DLP solution?
Comprehensive data coverage, precise data identification, granular policy management, real-time monitoring and enforcement, centralized management and reporting, incident response capabilities, user behavior monitoring, and integration with other security tools are important characteristics to search for in a DLP solution.
7: Can DLP prevent insider threats?
Yes, both intentional and unintentional insider risks can be avoided with DLP. DLP can identify and stop workers’ or contractors’ illegal attempts to access, copy, or send sensitive data by keeping an eye on user behavior and enforcing data handling regulations.
8: How is DLP different from data encryption?
By regulating how data is handled and sent, DLP aims to stop data loss or misuse. On the other side, data encryption safeguards data by rendering it unintelligible to unauthorized parties. DLP offers more extensive controls over data processing and consumption, whereas encryption protects data both in transit and at rest. Both of these are frequently employed as supplementary security measures.
9: What industries benefit most from DLP?
DLP is especially advantageous for sectors that manage substantial amounts of sensitive data and must adhere to stringent regulatory requirements. These include the fields of law, technology, government, healthcare, and finance. However, putting DLP into practice can help any firm that values its data and wishes to avoid breaches.
10: Is DLP only for large enterprises, or can small businesses use it too?
There are currently DLP solutions that meet the needs and budgets of small and medium-sized organizations (SMBs), whereas earlier DLP solutions were frequently costly and complex, making them better suited for large enterprises. For SMBs, cloud-based DLP solutions in particular provide more scalable and accessible possibilities.
11: What challenges are involved in implementing DLP?
The intricacy of deployment and configuration, the danger of false positives, the requirement for specialized knowledge, the possible influence on system performance, and user resistance are some of the difficulties that may arise while putting DLP into practice. To overcome these obstacles, careful planning, extensive testing, and staff training are essential.
12: Are there different types of DLP systems?
Indeed, DLP systems come in a variety of forms, such as cloud DLP (protecting data in cloud environments), network DLP (monitoring data in transit), endpoint DLP (protecting data on devices), and integrated DLP (features built into other security products).
13: How can companies ensure DLP compliance with regulations?
By tailoring their DLP policies to meet the particular criteria of certain regulations (such as the GDPR, CCPA, and HIPAA), businesses can guarantee DLP compliance. DLP solutions can assist in keeping track of data access and usage audit trails, detecting and stopping regulated data leaks, and producing reports for compliance.
14: Does DLP protect data on mobile devices and the cloud?
Yes, data that is accessed and stored on mobile devices and in cloud environments can also be protected by contemporary DLP solutions. This entails keeping an eye on data accessed via mobile apps, managing data synchronization with cloud services, and implementing rules for data kept in SaaS apps and cloud storage.
15: What are the common mistakes to avoid when deploying DLP?
When implementing DLP, some pitfalls to avoid include not understanding your data, implementing restrictive or complicated policies without doing adequate testing, ignoring employee training, not reviewing and updating policies on a regular basis, and not integrating DLP with other security solutions. For deployment to be successful, a stepwise approach and ongoing monitoring are necessary.
Conclusion
By 2025, data loss prevention will be a necessity for businesses rather than a luxury. Craw Security, the Best Cybersecurity Training Institute in India, highlights how important DLP is to creating a strong security posture. Businesses may successfully safeguard their priceless data assets in an increasingly complex digital environment by comprehending the significance of DLP, the many kinds of data loss and risks, how DLP operates, and the best practices for implementation. Purchasing the appropriate DLP solutions and knowledge is an essential first step in securing the future of your company.
To know more about our world-class Penetration Testing Services in India, you can give us a call at our 24X7 hotline mobile number +91-9513805401 and have a word with our superb penetration testers with more than 10 years of quality work experience.
Related
Leave a ReplyCancel reply
About Us
CrawSec, commonly known as Craw Security is a paramount cybersecurity training institution situated at Saket and Laxmi Nagar locations in New Delhi. It offers world-class job-oriented cybersecurity training programs to interested students.
Contact Us
1st Floor, Plot no. 4, Lane no. 2, Kehar Singh Estate Westend Marg, Behind Saket Metro Station Saidulajab New Delhi – 110030
+91 951 380 5401
[email protected]
HR Email : [email protected]
Trending Cyber Security Courses
One Year Cyber Security Course | Basic Networking with AI | Linux Essential | Python Programming | Ethical Hacking | Penetration Testing with AI | Cyber Forensics Investigation | Web Application Security with AI | Mobile Application Security with AI | AWS Security with AI | AWS Associate with AI | Red Hat RHCE | Red Hat RHCSA | Red Hat Open Stack | Red Hat RH358 | Red Hat Rapid Track | Red Hat OpenShift | CCNA 200-301 | CCNP Security 350-701 | CompTIA N+ | CompTIA Security+ | CompTIA Pentest+ | CompTIA A+ | CompTIA Cysa+ | CompTIA CASP+ | Pen-200 / OSCP | Pen-210 / OSWP | Reverse Engineering | Malware Analysis | Threat Hunting | CRTP | CISA | Certified Ethical Hacker(CEH) v13 AI | Certified Network Defender | Certified Secure Computer User | Eccouncil CPENT | Eccouncil CTIA | Eccouncil CHFI v11
Are you located in any of these areas
NARELA | BURARI | TIMARPUR | ADARSH NAGAR | BADLI | RITHALA | BAWANA | MUNDKA | KIRARI | SULTANPUR MAJRA | NANGLOI JAT | MANGOL PURI | ROHINI | SHALIMAR BAGH | SHAKUR BASTI | TRI NAGAR | WAZIRPUR | MODEL TOWN | SADAR BAZAR | CHANDNI CHOWK | MATIA MAHAL | BALLIMARAN | KAROL BAGH | PATEL NAGAR | MOTI NAGAR| MADIPUR | RAJOURI GARDEN | HARI NAGAR | TILAK NAGAR | JANAKPURI | VIKASPURI | UTTAM NAGAR | DWARKA | MATIALA | NAJAFGARH | BIJWASAN | PALAM | DELHI CANTT | RAJINDER NAGAR | NEW DELHI | JANGPURA | KASTURBA NAGAR | MALVIYA NAGAR | R K PURAM | MEHRAULI | CHHATARPUR | DEOLI | AMBEDKAR NAGAR | SANGAM VIHAR | GREATER KAILASH | KALKAJI | TUGHLAKABAD | BADARPUR | OKHLA | TRILOKPURI | KONDLI | PATPARGANJ | LAXMI NAGAR | VISHWAS NAGAR | KRISHNA NAGAR | GANDHI NAGAR | SHAHDARA | SEEMA PURI | ROHTAS NAGAR | SEELAMPUR | GHONDA | BABARPUR | GOKALPUR | MUSTAFABAD | KARAWAL NAGAR | GURUGRAM | NOIDA | FARIDABAD
Craw Cyber Security (Saket and Laxmi Nagar) is just a few kilometer’s drive from these locations.